Docker企业级私有仓库——Harbor介绍和部署
前言
docker容器应用及开发和运行离不开可靠的镜像管理,在前面的文章我们提到了我们在拉取镜像的时候使用的是docker官方提供的公共镜像仓库,但是无论从安全还是效率等其他方面考虑,我们还是需要部署在私有环境中的Registry。
而本文将介绍的是一款企业级docker镜像仓库Harbor的部署和使用,而且在之后的Kubernetes的集群中,也推荐使用Harbor仓库环境。
一、Harbor概念与特性简介
什么是Harbor?
Harbor是由VMware公司开源的企业级的Docker Registry管理项目,相比docker官方拥有更丰富的权限权利及完善的架构设计,适用于为大规模的docker集群部署提供仓库服务。其主要提供 了Dcoker Registry 管理界面UI,可基于角色访问控制、镜像复制、AD/LDAP 集成、日志审核等功能,并且完全支持中文。
Harbor有哪些特性?
- 基于角色的访问控制:用户与docker镜像仓库通过项目进行组织管理,一个用户可以对多个镜像仓库在同一命名空间里具备不同的权限;
- 镜像复制:镜像可以在多个Registry实例中复制(同步)。非常适合于负载均衡、高可用的混合或多云场景;
- 图形化用户界面:用户可以通过浏览器来进行相关的查看、检索、管理等操作;
- AD/LDAP支持:Harbor可以集成企业内部已有的AD/LADP,用于鉴权认证管理;
- 审计管理:所有针对镜像仓库的操作都可以被追踪记录;
- 国际化:支持英文、中文、德文、日文及俄文等的本地化版本,会陆续跟进加入;
- RESTful API:该接口提供给管理员对于Harbor更多的操控,管理更加方便容易;
- 部署简单:提供在线和离线两种方式,也可以安装到vSphere平台的虚拟设备。
二、Harbor架构与组件
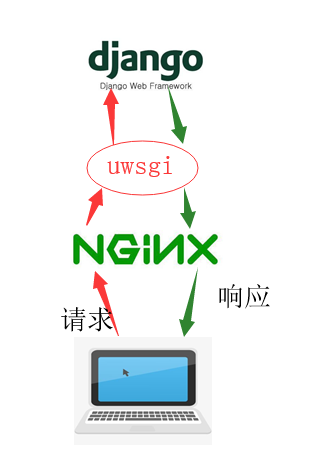
先来看看harbor整体的架构图

其实Harbor自有组件是上图中的Core Service所提供的核心功能,Replication Job Services所提供的多个Harbor实例之间的镜像同步(复制)功能以及Log collector提供的监控以及日志分析功能
其中核心服务主要是三个方面:
UI:提供图形化界面,帮助用户管理registry上的镜像(image), 并对用户进行授权。
webhook:为了及时获取registry 上image状态变化的情况, 在Registry上配置webhook,把状态变化传递给UI模块。
Auth服务:负责根据用户权限给每个docker push/pull命令签发token. Docker 客户端向Regiøstry服务发起的请求,如果不包含token,会被重定向到这里,获得token后再重新向Registry进行请求。
API: 提供Harbor 的RESTful API接口
而上图中其他的组件都是Harbor所依赖的外部组件,例如Nginx(做代理)、Registry v2(镜像仓库,官方负责存储镜像的位置)以及数据库等等
三、Harbor部署和测试流程
准备环境:一台部署好docker的虚拟机Centos7作为Harbor部署服务器,另一台也需要部署docker环境来作为客户端进行相关测试
具体规划:
服务端docker-harbor:192.168.0.135,Centos7操作系统,docker-ce(即docker环境)
、docker-compose、harbor
客户端(测试端):192.168.0.129;Centos7操作系统,docker-ce
服务端部署
下面开始进行部署配置
首先在harbor端安装配置docker-compose和harbor软件安装
可以通过curl命令下载(考验网速的时候到了~~):
下载docker-compose工具
curl -L https://github.com/docker/compose/releases/download/1.21.1/docker-compose-`uname -s-uname -m` -o /usr/local/bin/docker-compose
下载harbor软件包
wget http://harbor.orientsoft.cn/harbor-1.2.2/harbor-offline-installer-v1.2.2.tgz
[root@localhost opt]# ls
containerd docker-compose docker.sh harbor-offline-installer-v1.2.2.tgz rh
[root@localhost opt]# chmod +x docker-compose
[root@localhost opt]# cp -p docker-compose /usr/local/bin/
[root@localhost opt]# ls
containerd docker-compose docker.sh harbor-offline-installer-v1.2.2.tgz rh
[root@localhost opt]# tar zxf harbor-offline-installer-v1.2.2.tgz -C /usr/local/
[root@localhost opt]# cd /usr/local/
[root@localhost local]# ls
bin etc games harbor include lib lib64 libexec sbin share src
[root@localhost local]# cd harbor/
[root@localhost harbor]# ll
总用量 527664
drwxr-xr-x. 3 root root 23 4月 6 09:02 common
-rw-r--r--. 1 root root 1163 10月 20 2017 docker-compose.clair.yml
-rw-r--r--. 1 root root 1988 10月 20 2017 docker-compose.notary.yml
-rw-r--r--. 1 root root 3191 10月 20 2017 docker-compose.yml
-rw-r--r--. 1 root root 4304 10月 20 2017 harbor_1_1_0_template
-rw-r--r--. 1 root root 4345 10月 20 2017 harbor.cfg
-rw-r--r--. 1 root root 539885476 10月 20 2017 harbor.v1.2.2.tar.gz
-rwxr-xr-x. 1 root root 5332 10月 20 2017 install.sh
-rw-r--r--. 1 root root 371640 10月 20 2017 LICENSE
-rw-r--r--. 1 root root 482 10月 20 2017 NOTICE
-rwxr-xr-x. 1 root root 17592 10月 20 2017 prepare
-rwxr-xr-x. 1 root root 4550 10月 20 2017 upgrade
修改harbor配置文件harbor.cfg、使用给出的脚本启动harbor
[root@localhost harbor]# vim harbor.cfg 


在该过程中,应该不难发现是会下载镜像和运行相关的容器的,我们可以查看一下
[root@localhost harbor]# docker images
REPOSITORY TAG IMAGE ID CREATED SIZE
vmware/harbor-log v1.2.2 36ef78ae27df 2 years ago 200MB
vmware/harbor-jobservice v1.2.2 e2af366cba44 2 years ago 164MB
vmware/harbor-ui v1.2.2 39efb472c253 2 years ago 178MB
vmware/harbor-adminserver v1.2.2 c75963ec543f 2 years ago 142MB
vmware/harbor-db v1.2.2 ee7b9fa37c5d 2 years ago 329MB
vmware/Nginx-photon 1.11.13 6cc5c831fc7f 2 years ago 144MB
vmware/registry 2.6.2-photon 5d9100e4350e 2 years ago 173MB
vmware/postgresql 9.6.4-photon c562762cbd12 2 years ago 225MB
vmware/clair v2.0.1-photon f04966b4af6c 2 years ago 297MB
vmware/harbor-notary-db mariadb-10.1.10 64ed814665c6 2 years ago 324MB
vmware/notary-photon signer-0.5.0 b1eda7d10640 3 years ago 156MB
vmware/notary-photon server-0.5.0 6e2646682e3c 3 years ago 157MB
photon 1.0 e6e4e4a2ba1b 3 years ago 128MB
[root@localhost harbor]# docker ps -a
CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES
2bc676837f83 vmware/Nginx-photon:1.11.13 "Nginx -g 'daemon of…" 3 minutes ago Up 3 minutes 0.0.0.0:80->80/tcp, 0.0.0.0:443->443/tcp, 0.0.0.0:4443->4443/tcp Nginx
d1bb681c1bde vmware/harbor-jobservice:v1.2.2 "/harbor/harbor_jobs…" 3 minutes ago Up 3 minutes harbor-jobservice
da75599518b4 vmware/harbor-ui:v1.2.2 "/harbor/harbor_ui" 3 minutes ago Up 3 minutes harbor-ui
55da84f35f22 vmware/registry:2.6.2-photon "/entrypoint.sh serv…" 3 minutes ago Up 3 minutes 5000/tcp registry
9143d4b35f5a vmware/harbor-db:v1.2.2 "docker-entrypoint.s…" 3 minutes ago Up 3 minutes 3306/tcp harbor-db
fbf66bc6ea28 vmware/harbor-adminserver:v1.2.2 "/harbor/harbor_admi…" 3 minutes ago Up 3 minutes harbor-adminserver
e2ef481df1c7 vmware/harbor-log:v1.2.2 "/bin/sh -c 'crond &…" 3 minutes ago Up 3 minutes 127.0.0.1:1514->514/tcp harbor-log
可见下载了13个镜像并且运行了7个容器,其实这个时候harbor服务已经搭建完了,是不是简单到不可思议了呢?
既然上文说到harbor仓库不仅部署简单,而且可以通过web UI界面进行登录管理,那么我们如何登录呢?
这就还是需要回到harbor的配置文件中看了,我们使用cat harbor.cfg 命令查看一下结果如下图:

当然这个密码是初始密码,可以修改的
好了,我们现在使用浏览器输入IP地址进行登录验证
登录测试

登录结果:

以上,Harbor的仓库就构建完成了,下面我们在web ui界面上进行一下操作,然后在命令行终端进行相关的测试验证。
我们创建一个私有项目myproject,用于测试上传和下载镜像

在Harbor服务器节点上登录仓库,先登进去才可以进行操作的哈!
[root@localhost harbor]# docker login -u admin -p Harbor12345 http://127.0.0.1/
WARNING! Using --password via the CLI is insecure. Use --password-stdin.
WARNING! Your password will be stored unencrypted in /root/.docker/config.json.
Configure a credential helper to remove this warning. See
https://docs.docker.com/engine/reference/commandline/login/#credentials-store
Login Succeeded
服务端上传测试
现在测试拉取一个Nginx镜像然后使用tag命令设置一个副本进行上传测试
[root@localhost harbor]# docker pull Nginx
Using default tag: latest
latest: Pulling from library/Nginx
54fec2fa59d0: Pull complete
4ede6f09aefe: Pull complete
f9dc69acb465: Pull complete
Digest: sha256:86ae264c3f4acb99b2dee4d0098c40cb8c46dcf9e1148f05d3a51c4df6758c12
Status: Downloaded newer image for Nginx:latest
docker.io/library/Nginx:latest
[root@localhost harbor]# docker tag Nginx:latest 127.0.0.1/myproject/Nginx:v1
[root@localhost harbor]# docker images
REPOSITORY TAG IMAGE ID CREATED SIZE
127.0.0.1/myproject/Nginx v1 602e111c06b6 Less than a second ago 127MB
Nginx latest 602e111c06b6 Less than a second ago 127MB
...//省略多余内容
#上传命令执行
[root@localhost harbor]# docker push 127.0.0.1/myproject/Nginx
The push refers to repository [127.0.0.1/myproject/Nginx]
b3003aac411c: Pushed
216cf33c0a28: Pushed
c2adabaecedb: Pushed
v1: digest: sha256:cccef6d6bdea671c394956e24b0d0c44cd82dbe83f543a47fdc790fadea48422 size: 948验证结果
点击myproject之后可以查看刚刚建立的项目中对应的镜像、成员、日志等信息

以上对于服务端的测试就到这里,有兴趣的朋友可以自己再继续尝试其他操作
下面测试通过客户端登录,及远程访问harbor,毕竟企业中需要大家共享该仓库,而且有对于不同的部门和不同人的身份都有着各自的权限(由领导或者老板决定的)
客户机远程测试(拉取和上传测试)
客户机当前环境
[root@localhost opt]# docker images
REPOSITORY TAG IMAGE ID CREATED SIZE
[root@localhost opt]# docker ps -a
CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES
第一步先要指定私有仓库harbor服务器的位置,IP地址
~~~shell、
[root@localhost opt]# vim /usr/lib/systemd/system/docker.service

~~~shell
[root@localhost opt]# systemctl daemon-reload
[root@localhost opt]# systemctl restart docker.service
此时我们进行登录
[root@localhost opt]# docker login -u admin -p Harbor12345 http://192.168.0.135
WARNING! Using --password via the CLI is insecure. Use --password-stdin.
WARNING! Your password will be stored unencrypted in /root/.docker/config.json.
Configure a credential helper to remove this warning. See
https://docs.docker.com/engine/reference/commandline/login/#credentials-store
Login Succeeded
此时我们将刚刚创建的私有仓库的一个镜像拉取测试一下(结果对比如下)
[root@localhost opt]# docker images
REPOSITORY TAG IMAGE ID CREATED SIZE
[root@localhost opt]# docker ps -a
CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES
[root@localhost opt]# docker pull 192.168.0.135/myproject/Nginx:v1
v1: Pulling from myproject/Nginx
54fec2fa59d0: Pull complete
4ede6f09aefe: Pull complete
f9dc69acb465: Pull complete
Digest: sha256:cccef6d6bdea671c394956e24b0d0c44cd82dbe83f543a47fdc790fadea48422
Status: Downloaded newer image for 192.168.0.135/myproject/Nginx:v1
192.168.0.135/myproject/Nginx:v1
[root@localhost opt]# docker images
REPOSITORY TAG IMAGE ID CREATED SIZE
192.168.0.135/myproject/Nginx v1 602e111c06b6 5 days ago 127MB
此时你也可以在web ui界面中查看对应的日志记录,必然有对应的操作记录(上文说过的“审计”特性)。
拉取测试完成了,接下来进行客户端上传测试
先退出登录,拉取测试镜像
[root@localhost opt]# docker logout http://192.168.0.135
Removing login credentials for 192.168.0.135
[root@localhost opt]# docker images
REPOSITORY TAG IMAGE ID CREATED SIZE
192.168.0.135/myproject/Nginx v1 602e111c06b6 5 days ago 127MB
[root@localhost opt]# docker pull cirros
...//省略部分内容[root@localhost opt]# docker tag cirros:latest 192.168.0.135/myproject/cirros:v1
[root@localhost opt]# docker login -u admin -p Harbor12345 http://192.168.0.135
WARNING! Using --password via the CLI is insecure. Use --password-stdin.
WARNING! Your password will be stored unencrypted in /root/.docker/config.json.
Configure a credential helper to remove this warning. See
https://docs.docker.com/engine/reference/commandline/login/#credentials-store
Login Succeeded
[root@localhost opt]# docker push 192.168.0.135/myproject/cirros:v1
The push refers to repository [192.168.0.135/myproject/cirros]
858d98ac4893: Pushed
aa107a407592: Pushed
b993cfcfd8fd: Pushed
v1: digest: sha256:c7d58d6d463247a2540b8c10ff012c34fd443426462e891b13119a9c66dfd28a size: 943
我们直接通过日志验证,顺便查看之前的操作是否留有记录

至此,部署安装,服务端以及客户端的上传下载测试都顺利完成了,最后补充一下有关harbor的管理与维护的操作
Harbor管理及维护
配置文件修改或维护
修改harbor.cfg配置文件需要先停止所有的harbor实例并且更新配置文件后,再运行prepare脚本进行重新的加载配置,之后进行重新创建和启动harbor实例
1、关闭所有容器(对应结果就是停止和移除的现象)
[root@localhost harbor]# docker-compose down -v
Stopping Nginx ... done
Stopping harbor-jobservice ... done
Stopping harbor-ui ... done
Stopping registry ... done
Stopping harbor-db ... done
Stopping harbor-adminserver ... done
Stopping harbor-log ... done
Removing Nginx ... done
Removing harbor-jobservice ... done
Removing harbor-ui ... done
Removing registry ... done
Removing harbor-db ... done
Removing harbor-adminserver ... done
Removing harbor-log ... done
Removing network harbor_harbor
[root@localhost harbor]# docker ps -a
CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES
[root@localhost harbor]# docker-compose ps
Name Command State Ports
------------------------------
[root@localhost harbor]# vim harbor.cfg
[root@localhost harbor]# ls
common docker-compose.notary.yml harbor_1_1_0_template harbor.v1.2.2.tar.gz LICENSE prepare
docker-compose.clair.yml docker-compose.yml harbor.cfg install.sh NOTICE upgrade
[root@localhost harbor]# ./prepare
Clearing the configuration file: ./common/config/adminserver/env
Clearing the configuration file: ./common/config/ui/env
Clearing the configuration file: ./common/config/ui/app.conf
Clearing the configuration file: ./common/config/ui/private_key.pem
Clearing the configuration file: ./common/config/db/env
Clearing the configuration file: ./common/config/jobservice/env
Clearing the configuration file: ./common/config/jobservice/app.conf
Clearing the configuration file: ./common/config/registry/config.yml
Clearing the configuration file: ./common/config/registry/root.crt
Clearing the configuration file: ./common/config/Nginx/Nginx.conf
loaded secret from file: /data/secretkey
Generated configuration file: ./common/config/Nginx/Nginx.conf
Generated configuration file: ./common/config/adminserver/env
Generated configuration file: ./common/config/ui/env
Generated configuration file: ./common/config/registry/config.yml
Generated configuration file: ./common/config/db/env
Generated configuration file: ./common/config/jobservice/env
Generated configuration file: ./common/config/jobservice/app.conf
Generated configuration file: ./common/config/ui/app.conf
Generated certificate, key file: ./common/config/ui/private_key.pem, cert file: ./common/config/registry/root.crt
The configuration files are ready, please use docker-compose to start the service.
3、重启docker服务和容器服务
[root@localhost harbor]# systemctl restart docker
[root@localhost harbor]# docker-compose up -d
Creating network "harbor_harbor" with the default driver
Creating harbor-log ... done
Creating harbor-adminserver ... done
Creating registry ... done
Creating harbor-db ... done
Creating harbor-ui ... done
Creating Nginx ... done
Creating harbor-jobservice ... done
结果:
[root@localhost harbor]# docker-compose ps
Name Command State Ports
-------------------------------------------------------------------------------------------------------------------------
harbor-adminserver /harbor/harbor_adminserver Up
harbor-db docker-entrypoint.sh MysqLd Up 3306/tcp
harbor-jobservice /harbor/harbor_jobservice Up
harbor-log /bin/sh -c crond && rm -f ... Up 127.0.0.1:1514->514/tcp
harbor-ui /harbor/harbor_ui Up
Nginx Nginx -g daemon off; Up 0.0.0.0:443->443/tcp, 0.0.0.0:4443->4443/tcp,
0.0.0.0:80->80/tcp
registry /entrypoint.sh serve /etc/ ... Up 5000/tcp UI相关操作演示
主要是进行用户创建及测试
1、创建用户操作



以上就是简单的harbor仓库管理和维护介绍了。
谢谢阅读!