问题描述
一个 IP 地址通过 BruteForce 扫描 install.php Wordpress 文件来攻击我的服务器:
/var/www/vhosts/website1.tld/logs/access_ssl_log:104.248.227.52 - - [28/Jul/2021:08:27:33 +0200] "GET /wp-admin/install.php HTTP/1.1" 200 5503 "-" "Mozilla/5.0 (Macintosh; Intel Mac OS X 10_10_1) AppleWebKit/537.36 (KHTML,like Gecko) Chrome/39.0.2171.95 Safari/537.36"
/var/www/vhosts/website2.tld/logs/access_ssl_log:104.248.227.52 - - [28/Jul/2021:08:27:43 +0200] "GET /wp-admin/install.php HTTP/1.1" 403 5686 "-" "Mozilla/5.0 (Macintosh; Intel Mac OS X 10_10_1) AppleWebKit/537.36 (KHTML,like Gecko) Chrome/39.0.2171.95 Safari/537.36"
/var/www/vhosts/website3.tld/logs/access_ssl_log:104.248.227.52 - - [28/Jul/2021:08:27:35 +0200] "GET /wp-admin/install.php HTTP/1.1" 200 6290 "-" "Mozilla/5.0 (Macintosh; Intel Mac OS X 10_10_1) AppleWebKit/537.36 (KHTML,like Gecko) Chrome/39.0.2171.95 Safari/537.36"
/var/www/vhosts/website4.tld/logs/access_log:104.248.227.52 - - [28/Jul/2021:08:27:44 +0200] "GET /wp/wp-admin/install.php HTTP/1.1" 404 1296 "-" "Mozilla/5.0 (Macintosh; Intel Mac OS X 10_10_1) AppleWebKit/537.36 (KHTML,like Gecko) Chrome/39.0.2171.95 Safari/537.36"
/var/www/vhosts/website5.tòd/logs/access_ssl_log:104.248.227.52 - - [28/Jul/2021:08:27:41 +0200] "GET /wordpress/wp-admin/install.php HTTP/1.1" 404 6219 "-" "Mozilla/5.0 (Macintosh; Intel Mac OS X 10_10_1) AppleWebKit/537.36 (KHTML,like Gecko) Chrome/39.0.2171.95 Safari/537.36"
etc...
我如何阻止此操作?
请注意,install.php 也用于安装,因此我无法阻止任何请求!
感谢支持, 问候, 吉安·马可。
解决方法
使用正则表达式设置过滤器以发现 install.php 上的点击 然后在短时间内为大量点击创建监狱。 有点脏,但这个正则表达式可能有用:
_log:(<ADDR>).*GET.*install.php

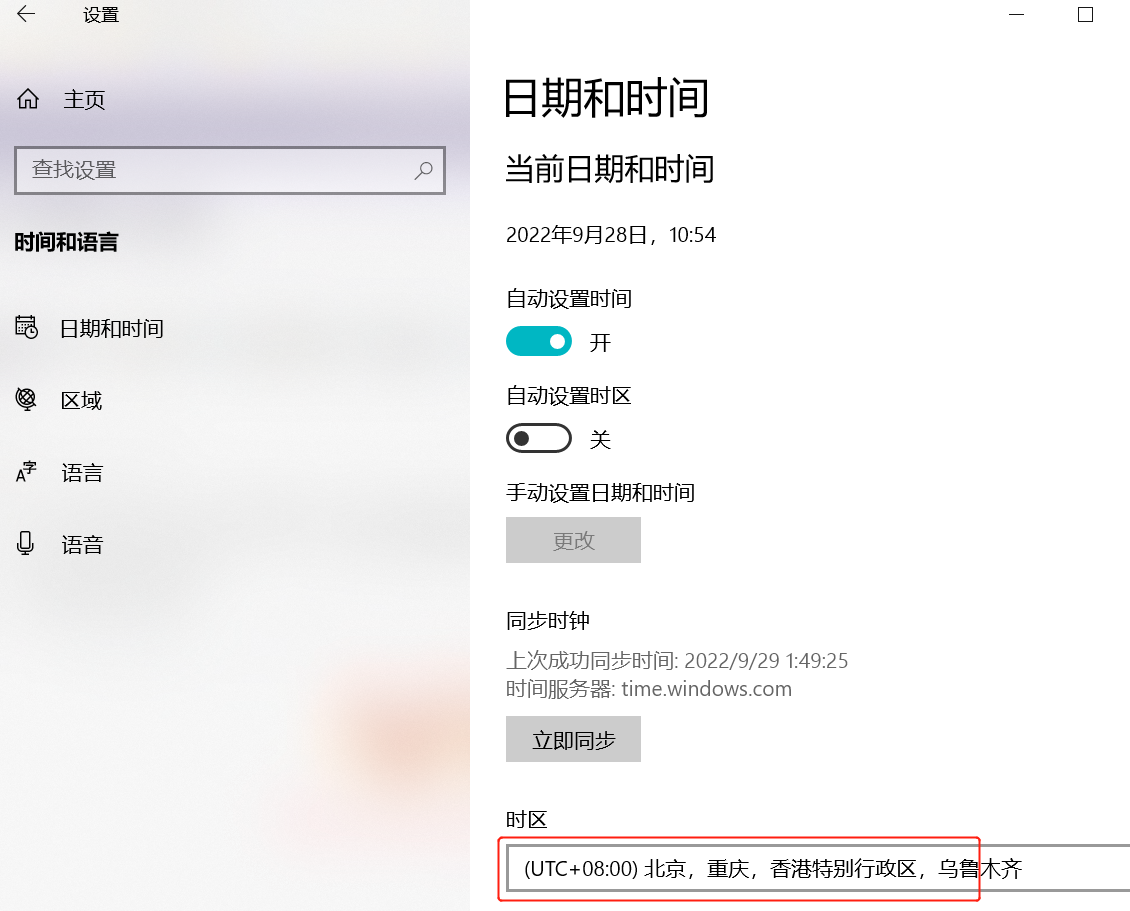 设置时间 控制面板
设置时间 控制面板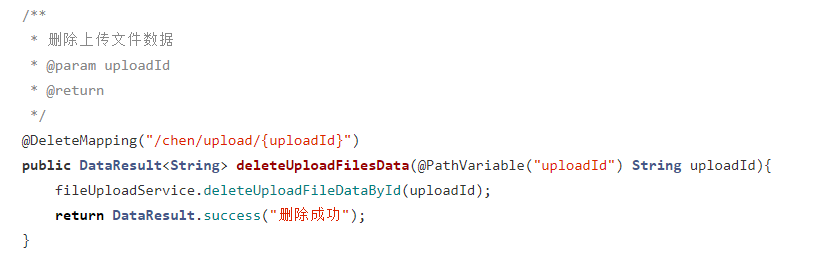 错误1:Request method ‘DELETE‘ not supported 错误还原:...
错误1:Request method ‘DELETE‘ not supported 错误还原:...